Insights
Security Defined Networking for Flexible and Highly Secure IT
New challenges call for new approaches. At present, for example, digitization requires an extensive restructuring of many business processes. IT departments are expected to flexibly support this dynamic development with the necessary applications. But that’s just one side of the story. On the other side, growing cyber threats demand additional security measures. In the past, increased IT security often came at the expense of flexibility in IT operations, however.
Experts search for answers among these conflicting priorities: How can the interests of both areas be taken into consideration? With the Security Defined Network concept, genua now presents a solution. In this interview, we ask Claas Lorenz, Technology Analyst at genua, how Security Defined Networking can be used to facilitate the balance between requirements from application operation and from the area of compliance.
Today we’re discussing IT security in corporate networks. Why should we talk about “Security Defined Networking” instead of about network security as in the past?
Claas Lorenz: Currently, the growth of networking, critical systems and sensitive data leads to a highly complex, difficult to comprehend IT landscape and, thus to greater risks than in the past. The methods of classic network security are thereby increasingly pushed to their limits. A new security approach is, thus, needed here. This already challenging situation is compounded by the need to find a balanced response to the different requirements that arise, on the one hand, from the business area, i.e., economic area, and, on the other hand, from the IT security. Security Defined Networking should make a significant contribution here.
Can you roughly describe the different requirements from the areas of application operation and IT security?
Claas Lorenz: In many companies, an imbalance exists between the budgeting of IT operation and IT security in favor of application operation. The benefits of investments and operating costs for the success of the business is simply more apparent in application operation – especially if no or little risk management is performed and only weak regulation is in place.
Another area of tension arises between data availability and data confidentiality. Although access restrictions serve to promote confidentiality, they inhibit availability. In practice, the decision is often made in favor of increased availability. Numerous data scandals in recent years can be attributed to insufficient or lenient access restrictions.
Another challenge: While regulation and risk management are quite stable and the requirements placed on compliance continue to develop at a moderate pace, a high dynamic exists in application operation. In addition, parts of the applications are often operated decentrally by individual departments; the IT security, on the other hand, is largely managed centrally.
Against this background, situations arise in which the IT security becomes a bottleneck during application operation. This then results in delays in making applications available for the business processes or in carelessness in the implementation of security measures and, thus, in a breach of compliance. What should only be temporary measures, such as network shares, become the rule and, over time, the IT security becomes a patchwork. If no explicit risk management with periodic compliance auditing takes place, successful cyberattacks are only a matter of time.
What contribution does Security Defined Networking make towards finding a solution to these conflicting goals?
Claas Lorenz: The described underbudgeting and relatively static nature of compliance result in long investment cycles in IT security. In practice, the dynamics in the evolution of the applications are not always incorporated. As a result, processes are implemented around the existing, centralized security infrastructure. This discrepancy can jeopardize the security of the entire company if so-called shadow IT is used, something which can be understood only with great difficulty centrally.
What conclusions can we draw from this? The security infrastructure should be designed flexibly, because at the time of planning all future requirements are not yet known. Security Defined Networking satisfies this requirement: The dynamics of the application evolution and processes are anticipated and supported in the best possible way by a flexible, scalable design of the security processes and infrastructure.
What does Security Defined Networking look like in practice?
Claas Lorenz: Introducing flexibility on the process and infrastructure level is achieved with Security Defined Networking by clearly separating the definition and the enforcement of security rules. Thus, unlike the current, purely central approach, parts of the policy definition can be delegated. For example, departments can create security rules that are appropriate for their applications. The security infrastructure for enforcing these rules is, however, managed centrally, thereby ensuring the central, permanent transparency of the network security and keeping the complexity of the infrastructure manageable.
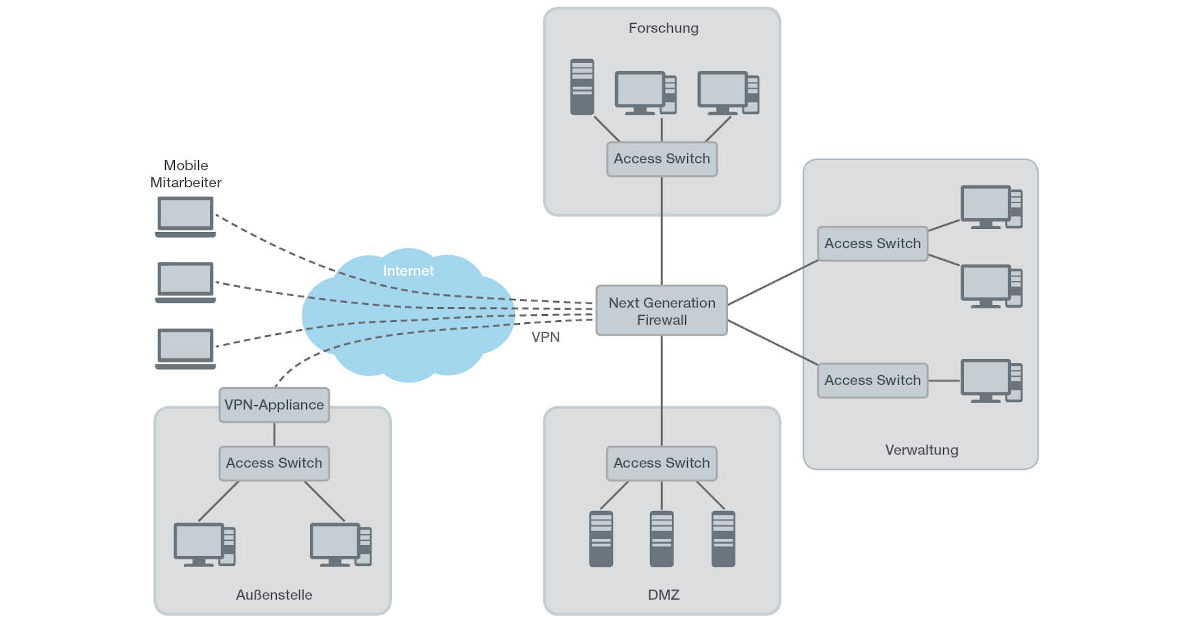
In concrete terms, this means: the security infrastructure is divided into macro- and micro-segments. Macro-segments correspond to the classic subnetworks and are centrally implemented using packet filter technology. Unlike classic setups with Next Generation Firewalls, however, they intentionally limit themselves in terms of the extent of the policies that they can enforce. The macro-segments provide a base level of security that does not impede the availability – or the performance – of the business applications.
The micro-segments, on the other hand, can be set up and enforced decentrally. The delegation of administrator rights all the way down to local responsibilities allows the configuration to be adapted to local requirements as appropriate for self-managed applications without undermining the entire security of the network. This is achieved by the macro-segments and, if necessary, other centrally specified policies in the micro-segments, but above all by global visibility of the data streams by monitoring in the micro-segments. Suspicious behavior can be detected close to the source, examined and, if necessary, contained and stopped.
Let’s talk about the actual implementation in the network: What differences arise here?
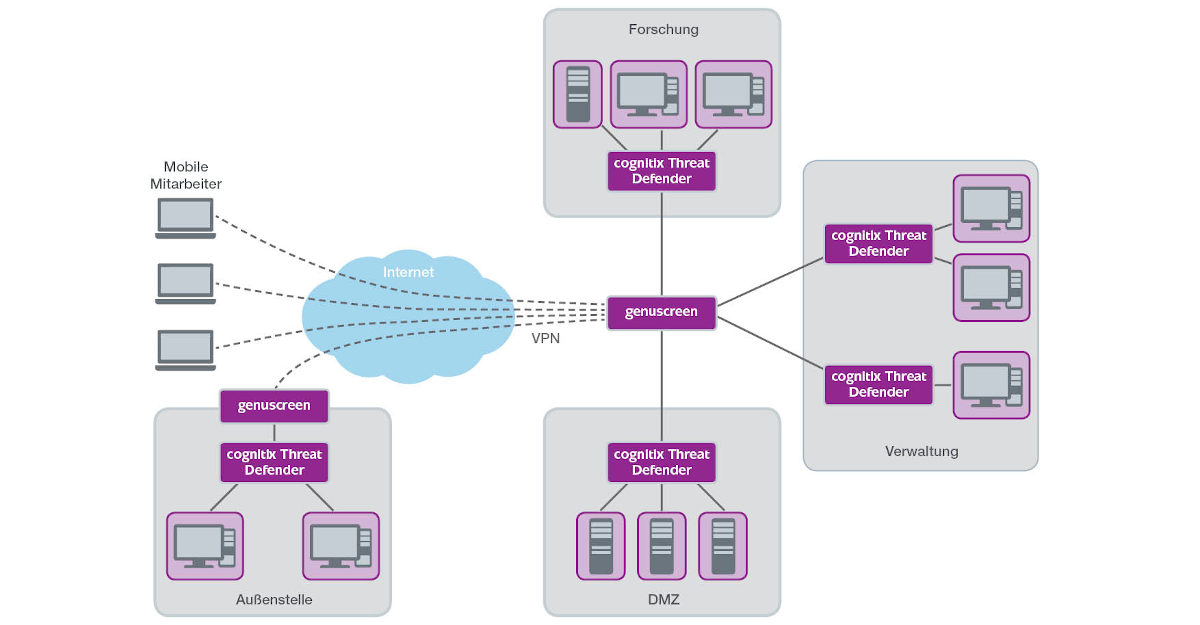
Claas Lorenz: One significant difference with respect to classic networks is that the micro-segmentation is performed in the access network of all end devices in the company. Instead of the typical access switch, lightweight, programmable appliances such as the cognitix Thread Defender are used that can perform the segmentation individually and automatically all the way down to the application layer.
The macro-segmentation at the perimeter, on the other hand, focuses on general connectivities between large security units. For example, it is permissible to access services in the DMZ from the internet, while attempts to access hosts in the research network should always be prevented. These policies are relatively stable over time and are easy to describe. An audit is greatly simplified by this approach. At the same time, the probability of the security solution impeding the availability of the business applications is reduced.
"With Security Defined Networking, the various interests from the areas of application operation and IT security are largely balanced."
Stricter policies can be implemented within the micro-segments. Here, one can decide whether to intervene in the network traffic proactively or reactively. The advantage of proactive security rules is that potentially malicious communication cannot occur in the first place. On the other hand, filtering may be too strict under certain circumstances, causing the availability of the business applications to suffer. This can be remedied by shifting towards reactive security rules that attempt to detect and subsequently prevent malicious communication. The availability of applications is thereby only restricted in the event of detected attacks.
Coming back to the beginning of the conversation: The process orientation of Security Defined Networking and the flexibility in the technical configuration using proactive and reactive security rules thus allow for balancing of the protective goals, of the application availability and of the necessary administration resources. The ability to delegate responsibilities enables local optimization to the needs of the respective users without having to sacrifice the central transparency. With Security Defined Networking, the various interests from the areas of application operation and IT security are largely balanced.
Thank you for the conversation.