IDS & IPS cognitix Threat Defender
![[Translate to English:] [Translate to English:]](/fileadmin/_processed_/8/c/csm_cognitix-threat-defender-visual_37c58ee717.png)
High-Performance Attack Detection for Reliable Protection of IT and OT Networks
cognitix Threat Defender provides visibility of all network traffic and supports network security by identifying attacks, detecting anomalies, and thus providing comprehensive protection against threats.
As an intrusion detection system (IDS), cognitix Threat Defender recognizes attempted attacks and enables targeted countermeasures. Using deep packet inspection, it identifies and inspects data packets and uses micro-segmentation to prevent the spread of external and internal attacks.
With regard to response and recovery, cognitix Threat Defender reacts to anomalies as an intrusion prevention system (IPS) and also provides valuable network information for forensic analyses.
Top Highlights
Your Benefits at a Glance
- Intrusion detection and filtering at network level (Layer 2) and application level (Layer 7)
- Market-leading real-time traffic database with more than 3,700 applications/apps and protocols
- Efficient threat detection based on signatures, rules, and behavioral analysis via baselining
Sophisticated threat detection engine examines network traffic by correlating it with tens of thousands of threat indicators
- High information value through clear graphical presentation, logging, and drill-down reporting
- Local and cross-site monitoring and reporting options through easy connection of third-party software
- Interfaces for flexible integration into the Security Operation Center (SOC) and connection to alerting, SIEM, and monitoring tools such as Splunk or Elastic
- Support for organizational reviews and audits such as ISO, ISMS, and IEC
- Protection of privacy through legally secure, GDPR-compliant application
- The solution and application concept allow customer-specific operation and thus ensure the user 100% data sovereignty
- genua promotes digital sovereignty through backdoor-free development "Made in Germany"
Comprehensive Protection
Maximum Availability and Security for Your Assets
With cognitix Threat Defender you increase the security and availability of assets in IT and OT networks within an intrusion detection ecosystem.
As an intrusion detection system (IDS), cognitix Threat Defender correlates network traffic with thousands of attack patterns for accurate attack detection. In addition, it can optionally be used as an intrusion prevention system (IPS) to protect your assets in the network at all times without manual intervention and to prevent damage.
Attack Detection & Defense
Correlation of Network Traffic with Tens of Thousands of Threat Indicators
IT teams need to stay up-to-date on the current threat situation in order to be able to optimally protect their infrastructure.
cognitix Threat Defender offers an extensive Indicators of Compromise (IoC) database and a Suricata-compatible IDS engine with a predefined and flexibly expandable rule set. Database and IPS rule set are continuously updated.
Its threat detection engine continuously compares network traffic against threat indicators and IPS rules. This can be done for the purpose of network monitoring (IDS), but also, for example, to automatically block suspicious traffic (IPS).
Use Case "Sensor"
Attack Detection: cognitix Threat Defender as Sensor according to the German "IT-Grundschutz Manual"
cognitix Threat Defender can gradually increase the security in a network of an authority, a critical infrastructure organization or a company that is structured according to the German "IT-Grundschutz Manual". As the basis for internal network protection, cognitix Threat Defender is placed at the firewall at the zone transition to the internal network. There it analyzes the data traffic in depth for anomalies.
For additional transparency and security, cognitix Threat Defender can also be placed in vulnerable areas – in this use case in DMZ A and in the network segments A and C. If the Internet front end, the servers or the clients have been successfully attacked, this can be detected with cognitix Threat Defender. The affected area can be isolated in real time to prevent lateral movement attacks.
Depending on the reaction strategy, the defensive task can be initiated by an alert (IDS) or an active intervention (IPS) by the particular instance of cognitix Threat Defender.
Use Case "Sensor in OT Networks"
Attack Detection: cognitix Threat Defender as Sensor in OT Networks
With the introduction of the Industrial Internet of Things (IIoT), it is becoming increasingly important to detect anomalies in production networks such as malware or unauthorized activities.
For this purpose, this application scenario provides sensors on the mirror port of the switches with regard to metadata traffic for the next higher network level. At the management level, the sensor data recorded by the cognitix Threat Defender instances is processed and evaluated by a Security Information and Event Management (SIEM).
Due to special security precautions, e.g. with industrial firewalls that isolate certain network segments, no active intervention by cognitix Threat Defender as an intrusion prevention system (IPS) is used in this scenario.
Contact Us for a Trial Period
Request a trial of cognitix Threat Defender to comprehensively evaluate features such as attack detection, automated response to anomalies, or micro-segmentation within your IT and OT infrastructure. We offer consulting, product instruction, service, and support for the implementation according to your individual requirements. Contact us!
Comprehensive Monitoring
Comprehensive Monitoring: Detailed Evaluations and Seamless Integration
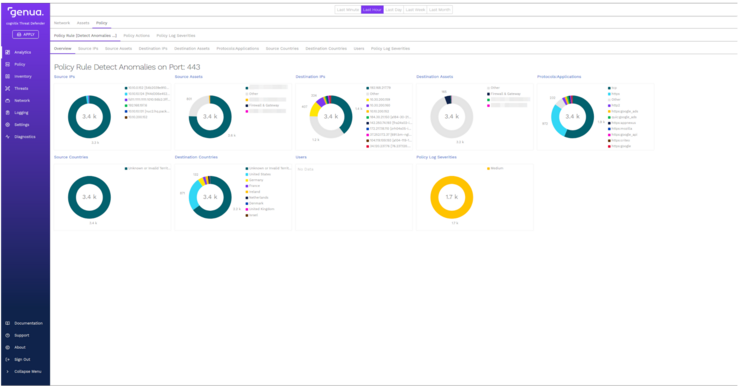
All network data is consolidated and visualized in a central overview with a modern user interface. Forensic investigations and rapid root cause identification are supported by in-depth analytics. Drill-down reporting allows individual events to be traced down to the packet level.
cognitix Threat Defender enables flexible data sharing: The collected information can be transmitted directly to existing alerting, SIEM, and monitoring solutions (e.g. Splunk, Elastic) via standardized interfaces. Monitoring works both locally and across multiple locations, ensuring you maintain a complete overview of your entire network at all times.
New: cognitix Threat Defender Protokolldatensensor
Capturing all communication relationships between network components and forwarding them to a SIEM enable real-time threat analysis.
If data from different local networks is correlated in a SIEM for central security monitoring, the data collection in the networks should be carried out using a sensor that is as non-reactive and lightweight as possible, operates transparently, and can be flexibly integrated.
The cognitix Threat Defender Protokolldatensensor meets this requirement. It captures metadata from all network data streams and provides it in an optimized format, such as Elastic, for direct import into a SIEM.