Insights
Post-Quantum Cryptography
Watch Out, Crypto Hackers: The Gradual Progression to Quantum-Safe Cryptography
With the quantum age fast approaching, the cryptographic encryption techniques used must meet higher and higher requirements. We must counter this threat today to ensure the integrity of online data in the future. The good news: The first quantum-safe solutions are in sight.
Cryptography is a crucial foundation for IT security. To protect confidential communications, financial transactions and critical infrastructure even in the coming quantum age, quantum-safe encryption is needed as soon as possible. After all, quantum computers already pose a threat to the current encryption algorithms – and not only because massive amounts of sensitive data are already being stored so that they can be decrypted in the future using suitable tools.
What is Quantum-Safe Encryption?
A theoretically fully secure encryption is only possible using quantum cryptography, i.e. based on physical principles. However, in practice, implementing this kind of encryption is not yet possible because it would require specialized equipment that is not (yet) viable and will be rather expensive in the future. Moreover, quantum cryptography is suitable only for particular applications. Therefore, researchers are developing brand-new algorithms that can withstand attacks by quantum computers and be implemented on classic hardware – this is post-quantum cryptography. However, certain things need to be done before these algorithms can be used in protocols and IT solutions.
RSA, AES, and More: Cryptographic Techniques and Keys
We visit websites, shop and carry out banking activities online or work from home via a VPN connection to the work network. This is all made possible by encryption and signature methods operating in the background – they verify the authenticity of the sender and ensure that the data cannot be read, or even tampered with, as it is transmitted between the sender and the recipient.
A cryptographic key can be used to turn plain text into an encrypted message for this purpose. Based on the type of key distribution, a distinction is made between symmetric and asymmetric techniques. In practice, the two techniques are often combined – usually, the key is exchanged via an asymmetric technique and the plain text is then encrypted via a symmetric technique.
Asymmetric techniques include the common RSA algorithm (named after the developers: Rivest, Shamir and Adleman), which is used to secure online orders and debit card payments, among other things, and is based on the factorization of prime numbers. Another technique is the Diffie-Hellman key exchange, which is based on discrete logarithms. Both techniques involve trapdoor functions. These functions are easy to compute but time-consuming to invert. The Advanced Encryption Standard (AES) is a symmetric encryption technique and offers a high degree of security due to its long key length of 128, 192 or 256 bits. For this reason, AES-192 and AES-256 are approved for US state documents with the highest level of confidentiality.
Quantum Computers: The New Crypto Hackers

What happens now if powerful quantum computers are used as code breakers? Grover's quantum algorithm is a search algorithm that can be used to search an unstructured database for one or more elements that meet a specific criterion. It speeds up the key search significantly and initially weakens symmetric techniques. Using correspondingly long keys neutralizes the threat for the time being.
The situation is different with asymmetric techniques. Quantum mechanical effects – such as superposition and entanglement – enable parallelism, thereby speeding up some calculations. Shor's algorithm can be run on a quantum computer to perform the prime factorization in comparatively little time – and other asymmetric techniques (such as Diffie-Hellman) would also be broken quickly.
Stored Today, Decrypted Tomorrow?
But quantum computing is still at a developmental stage, so why worry about it now?
There are several good reasons.
With technology giants such as IBM, Amazon and Google investing heavily in work on quantum computers, it is only a matter of time until the latter find their way out of the research labs and into applications – experts predict that this will happen in the early 2030s.
However, sensitive data is already in danger: Intelligence services worldwide are storing encrypted confidential data with the intention of using quantum computers to decrypt it at some point in the future. Governmental and military communications may be targeted at first, but as the technology becomes more advanced, many more targets will be affected. Therefore, appropriate preparations must be made today to ensure that sensitive data remains protected in the future.
The good news: There are already viable options for gradually making the cryptographic infrastructure quantum safe.
It is unclear when quantum computers will be available. Today's quantum computers have the character of laboratory experiments and do not yet play a role in practice. But what has already been achieved today was questioned just a few years ago. Accordingly, it seems realistic that a sufficiently large quantum computer relevant to cryptography could be created within the next ten years. The responsible authorities, such as the German BSI, are therefore using the working hypothesis that everything must be secured in a quantum-resistant manner by the early 2030s at the latest.
Post-Quantum Cryptography: Balancing Security and Efficiency
Post-quantum cryptography (PQC) is based on mathematical problems that are theoretically impossible to solve in a reasonable amount of time even with quantum computers. A variety of approaches are being taken. For example, the techniques may rely on one of the following:
The difficulty of efficiently deciphering general error correcting codes
The difficulty of specific problems in mathematical grids
The security features of the hash functions used
Hash functions are considered sophisticated quantum-computer-resistant signature schemes. The signature scheme XMSS was developed during the research project squareUP. Since 2018, it has officially been the permissible Internet standard (cf. RFC 8391) and even authorities consider it fit for use (cf. PDF: BSI TR-02102-1). XMSS uses hash functions that create a type of verifiable digital fingerprint from the file or message to be sent – but it is only suitable for digital signatures. Code-based, grid-based and other techniques can be used for encryption but are not always good for signatures.
So there will not be a single solution to all cryptography problems. These techniques also pose the following additional challenges:
Key lengths are significantly longer than with classic techniques, therefore requiring more storage space
In some cases, encryption and decryption would require a lot of computing power, which would massively decrease the efficiency of many current applications.
Quantum Resistant Key Exchange Techniques

The first step toward quantum-safe cryptography was the abovementioned hash-based signatures for software updates. These signatures are particularly relevant because they verify the authenticity of the sender or manufacturer while also ensuring that an update cannot be tampered with from outside the system.
Quantum-resistant key exchange techniques are far more complex. One example application is secure communication via Virtual Private Networks (VPNs). VPNs were researched as part of the project QuaSiModO – Quantum-Safe VPN Modules and Operation Modes – which was funded by the German Federal Ministry of Education and Research (BMBF) and carried out in consultation with the BSI.
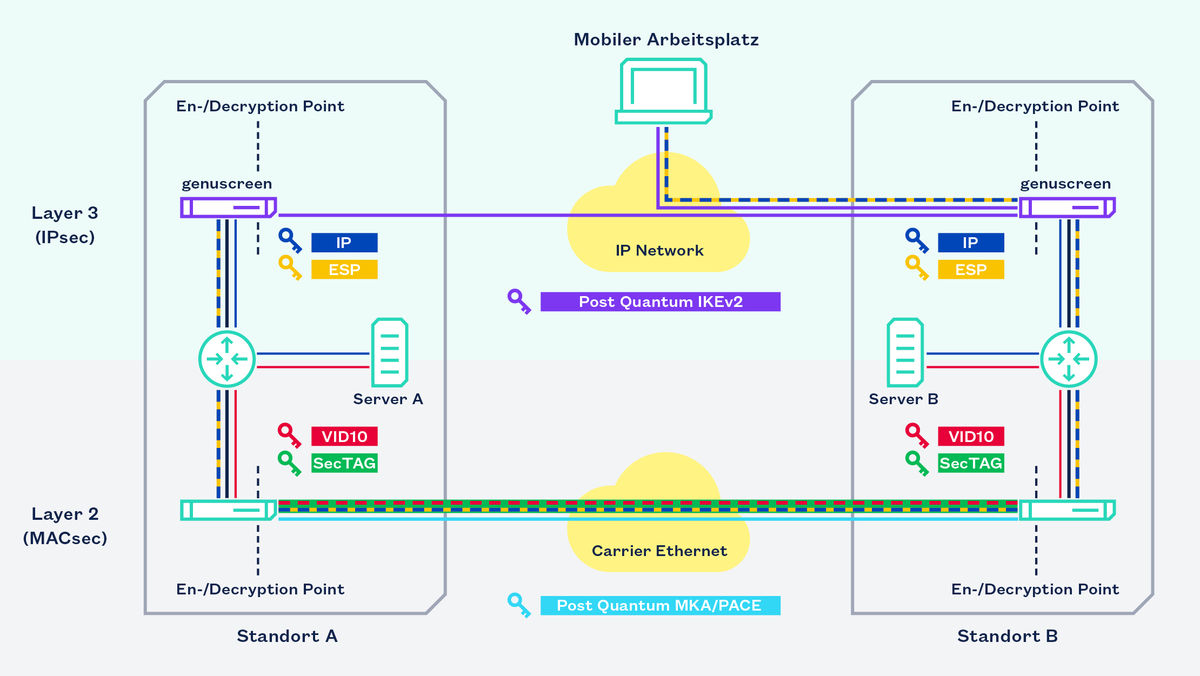
Many VPN protocols differentiate between the actual communication channel, which is typically secured using symmetric techniques, and (other) key exchange or key agreement protocols. Particularly in the latter case, it depends on the currently used cryptographic techniques. The key exchange protocol used most frequently in the context of IPsec is Internet Key Exchange version 2 (IKEv2), which is based on a Diffie-Hellman key exchange. This protocol must be replaced with or supplemented by quantum-resistant techniques. Problems such as the limitation of the overall key size and other special features resulting from the fragmentation require the sophisticated integration and handling of new techniques.
Therefore, the QuaSiModO research project tested initial drafts of Internet standards in practice and evaluated different cryptographic techniques from the NIST competition as a quantum-safe expansion of IKEv2. Specifically, the aim was to identify practical trustworthy and secure algorithms that can be used to operate quantum-safe VPNs in the near future. The common IPsec and MACsec key exchange and key agreement protocols, Internet Key Exchange Version 2 (IKEv2) and MKA/PACE, should be made quantum-safe for this purpose, including by using hybrid, cryptoagile, and multilayer encryption techniques. In addition, the first attempts at post-quantum authentication have been undertaken. genua's main research had been on IPsec protocols.
The first pre-quantum solutions are already available on the market: For example, the update mechanism of the Firewall & VPN-Appliance genuscreen as both a digital signature and a quantum-resistant signature.
Thus, increasingly effective quantum-resistant solutions are to be developed gradually in consultation with the BSI and the NIST, or rather the protocols are to be adapted based on the new standards. However, when fully quantum-resistant products will be available on the market also depends on the standardization process.
The New World of the Quantum-Safe Future – Complex but Agile
What awaits us in the quantum-safe (IT) world? Will we be safe from attacks and security apocalypses? Unfortunately not, as there will always be dangerous attacks and crypto bugs. But with post-quantum cryptography, the incidents will not be so serious. The probability of fatal errors is low, since communication will be protected by techniques operated in parallel.
In addition, agility will be greater: If the protocols are not designed too specifically for one technique, a system administrator can immediately switch to a different protocol with sufficient security if needed, until the defective protocol has been repaired. However, a lot of research is needed before the quantum-safe (IT) future arrives.
With the quantum-resistant key exchange for IPsec and MACsec, the implementation of quantum-resistant solutions on Layer 2 and Layer 3 of the TCP/IP reference model and the development and testing of VPN-suitable hybrid and cryptoagile mechanisms, we have achieved all the goals of our QuaSiModO research project.
In addition to genua as project coordinator, the QuaSiModO research project, which ran from 2019 to the start of 2023 and was funded by the German Federal Ministry of Education and Research (BMBF), involved the following project partners: ADVA Optical Networking SE, the Fraunhofer Institute for Applied and Integrated Security (AISEC) and the Ludwig Maximilian University of Munich (LMU). The German Federal Office for Information Security (BSI) and the Hessen CyberCompetenceCenter (Hessen3C) were also associated partners.
Sources and related links
[1] squareUp research project
[3] BSI-Technische Richtlinie: Kryptographische Verfahren: Empfehlungen und Schlüssellängen (BSI Technical Guideline: Cryptographic Mechanisms: Recommendations and Key Lengths, German only)
[4] NIST: Post-Quantum Cryptography Standardization (https://csrc.nist.gov/Projects/post-quantum-cryptography/Post-Quantum-Cryptography-Standardization)
[5] Migration zu Post-Quanten-Kryptografie“ des Bundesamts für Sicherheit in der Informationstechnik (BSI), Handlungsempfehlung des BSI, Stand 2020 (German Federal Office for Information Security (BSI): Migration to Post Quantum Cryptography: Recommendations for action by the BSI, dated 2020, German only)
[6] QuaSiModO research project

